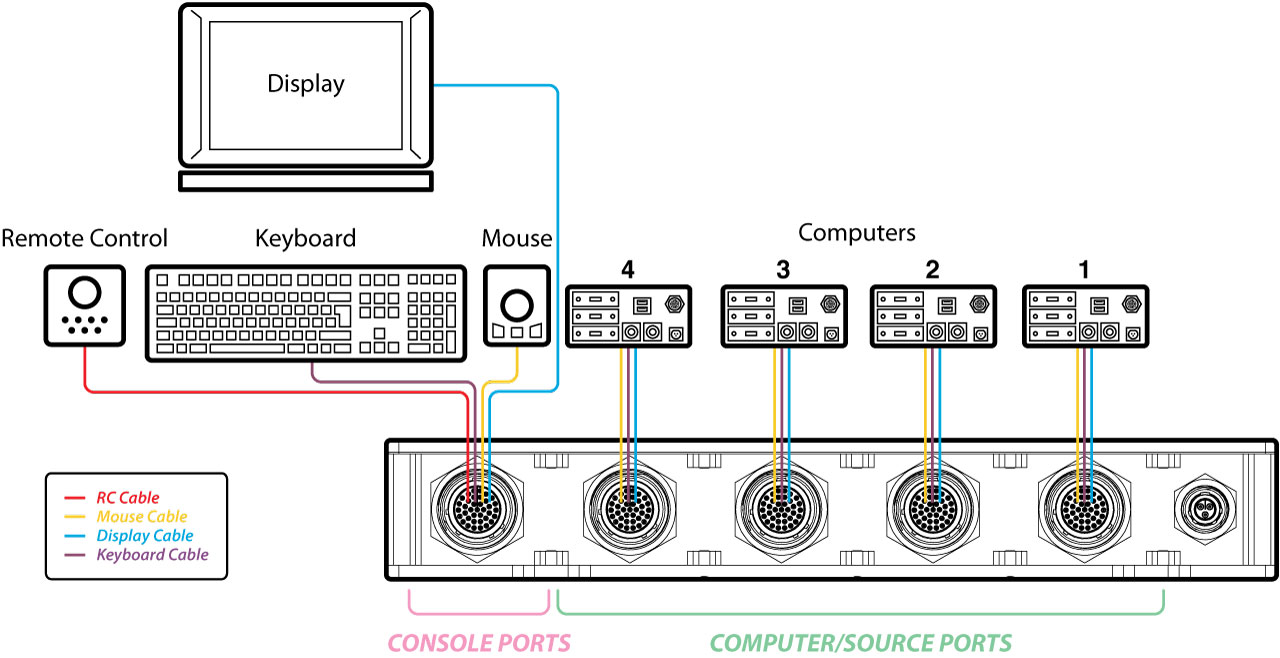
Secure rugged 4-Port KVM Switch
The SK41D-4TR, HSL’s 4-Port HDMI Rugged secure KVM Switch, provides military users with superior security under the most challenging environmental conditions. The SK41D-4TR is the only KVM switch in the world that is both NIAP PP 4.0 certified and is Tempest level A compliant. It designed to be installed on military vehicles, marine vessels and airborne platforms.
For easier mounting and better situational awareness, the SK41D-4TR is optionally equipped with a remote control that can be mounted on the operator dashboard.
KVM device models addressed in this page:
- SK41D-4TR – Secure MIL-STD TEMPEST 4-Port HDMI KVM Switch
- WR40-4TR – WR40-4TR Remote Control for SK41D-4TR Secure KVM
MODELS
SPECIFICATIONS
DOWNLOADS
RELATED PRODUCTS
You may also like…
-
SECURE 8 PORT DUAL-HEAD KVM SWITCHES
This product has multiple variants. The options may be chosen on the product page -
SECURE 8 PORT SINGLE-HEAD KVM SWITCHES
This product has multiple variants. The options may be chosen on the product page -
SECURE 4 PORT SINGLE-HEAD KVM SWITCHES
This product has multiple variants. The options may be chosen on the product page