SoundSentry™ Secure Meeting Room Solutions
Harden Any meeting room, Secure every conversation.
Same space. Same equipment. No risk.
One room, Any Classification
Hardware-level Data Security
Retrofit-ready Architecture
Seamless Security Level Switching
SoundSentry™ secures any meeting room, enabling classified and unclassified discussions in the
same space with uncompromising protection of sensitive information. It integrates easily into
existing infrastructure or serves as the core of new high-security environments.
Uninvited threats have joined your meeting
Network infiltration
Compromised guest devices gain direct access to secure networks by exploiting KVM switch and peripheral device vulnerabilities.Peripheral surveillance
Microphones, speakers, displays and cameras can be exploited for persistent eavesdropping, malicious code injection and data exfiltration.Acoustic exploitation
Speakers deliver high-frequency audio signals to exfiltrate data.
Personal devices
- Data Extraction
- UMalware Injection
Videobar
- High-frequency data transfer
- Eavesdropping
- Unauthorized Bluetooth connections
- Wifi Data Breaching
- Storage attacks
SmartTV
- Wifi Data Breaching
- Unauthorized Bluetooth connections
- Compromised USB devices
- Storage-based attacks
Commercial KVM
- Compromised USB devices
Introducing SoundSentry™
SoundSentry is the world’s only solution specifically designed to enable discussions of any classification level in a single, dual use meeting room with a seamless transition between modes.
By introducing hardware-level measures to the conferencing infrastructure, any meeting room can be hardened against data breaches
and eavesdropping attempts.
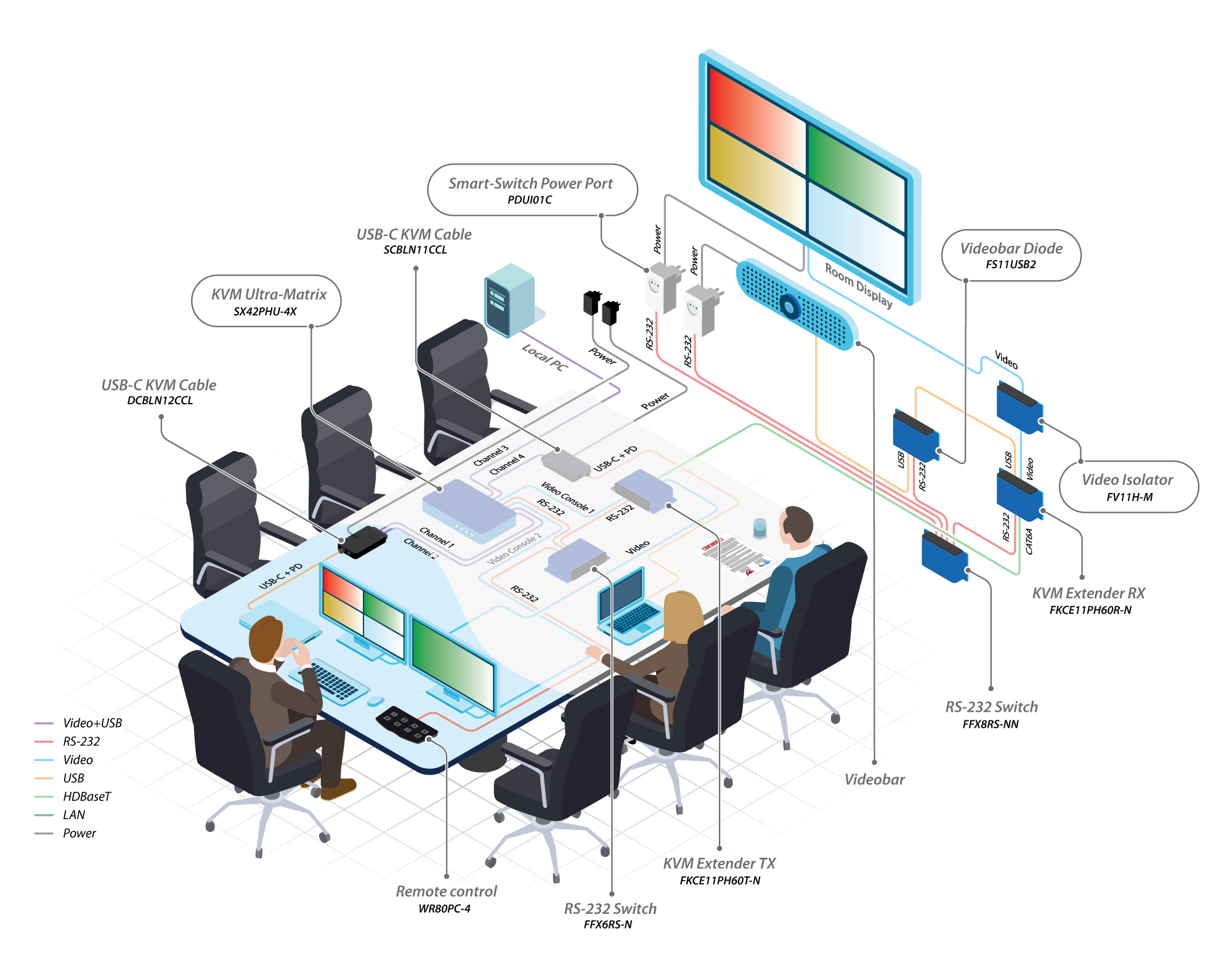
SoundSentry includes these key components for a secure meeting room setup:
Adaptive Configuration to Dynamic Environments
SoundSentry can be integrated into any meeting environment. From executive offices to boardrooms, each comes with its
own set of vulnerabilities.
Explore the use cases how SoundSentry addresses each attack surface:
Share Peripherals. Not Data.
SECURE PERIPHERAL SHARING – Share a single set of peripherals across multiple air-gapped networks and classification levels. HSL’s NIAP-certified KVMs enforce absolute data isolation, making data leakage between sources impossible.
UNIDIRECTIONAL, WIRED DATA FLOW – Eliminate hardware-level data breaches with HSL’s media diodes. These create a physically enforced, unidirectional data path, making it impossible for data to leak back from a media device to the source computer.
SMART POWER-MANAGEMENT – Instantly harden meeting room security by cutting power to vulnerable peripherals like displays and videobars. This offers a true hardware disconnect, a level of security that simply muting a device cannot provide.