VoIP Phones Protection
Brief:
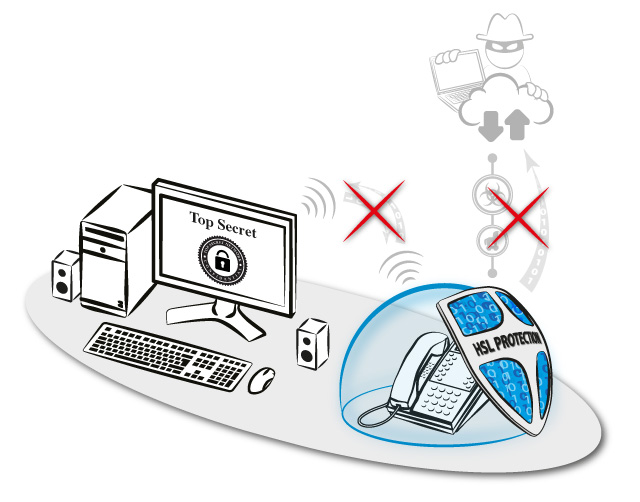
VoIP phones are everywhere – even in the most classified offices and meeting rooms. Although being exposed to the outside world through networks that have internet access VoIP phones are not perceived as a security threat. HSL VoIP Phone Protection Solution is designed to mitigate threats such as eavesdropping by preventing a remote attacker from exploiting the phone to listen to surrounding classified conversations.
Challenge:
VoIP phones are vulnerable to computer attacks as they run all-purpose computer hardware and have limited (if any) hardware and software protection.
Users and administrators are often unaware of eavesdropping threats as there is no evidence of the phone being tampered.
The Risk:
Eavsedropping: A remote attacker can activate the phone’s microphones from remote to eavesdrop conversations taking place at the vicinity of the phone.
Breaching Air Gapped Networks: Researches show that breaching air-gapped networks can be achieved by compromising a computer to transcode and transmit confidential data over-the-air as audio.
A compromised VoIP phone can intercept/generate audio signals to communicate with an air-gapped computer and thus breach the network.
Solution:
HSL Secure VoIP Implant: The HSL Secure VoIP Implant is a hardware implant which is securely embedded inside a standard VoIP telephone.
The Secure VoIP Implant is designed to mitigate eavesdropping and prevent a remote attacker from exploiting the phone to listen to surrounding classified conversations.
The implant allows normal phone operation without any negative effect on performance or user experience. Audio and visual notifications provide clear and simple user indications of the phone’s secure state.

