SoundSentry™ Solution for Secure Meeting Rooms
Brief:
Meeting rooms are a hub for secure, proprietary, confidential and non-classified communications. This nexus of information is an attractive target for bad actors seeking to gain sensitive information through cyber-attacks that include data breaches and eavesdropping. The SoundSentry product family protects sensitive meetings from these threats, while facilitating simple operation, even when conducted in a cross-domain environment.
Challenge:
Peripherals like the keyboard and mouse, display screens and videobars, are commonly shared between the computers of meeting room participants, along with multi-domain sources that may be accessed during meetings. Guest computers that connect to a KVM switching matrix, impose a security threat to all computers and networks that share the same switch and peripherals. Smartphones, a device found in every participant’s pocket, pose eavesdropping challenges to the meeting.
The Risk:
Computer peripherals typically have no security mechanisms (anti-virus, firewall, user permissions, etc.) making them vulnerable to malicious attacks. Shared peripherals can be used to breach the gap between secluded networks. Advanced hacking techniques can retask audio speakers into microphones that record and transmit conversations or into high frequency modems for transmitting data to a malicious actor. Microphones and cameras that are inadvertently left on or hacked can transmit audio and video of sensitive conversations without the participants’ knowledge. Peripheral devices with internal memory and back-up batteries, like videobars and display screens, can be used as intermediary devices for storing information that is later transmitted outside the organization. Smartphones can be hacked to record and transmit conversations, even if the devices are switched off.
Solution:
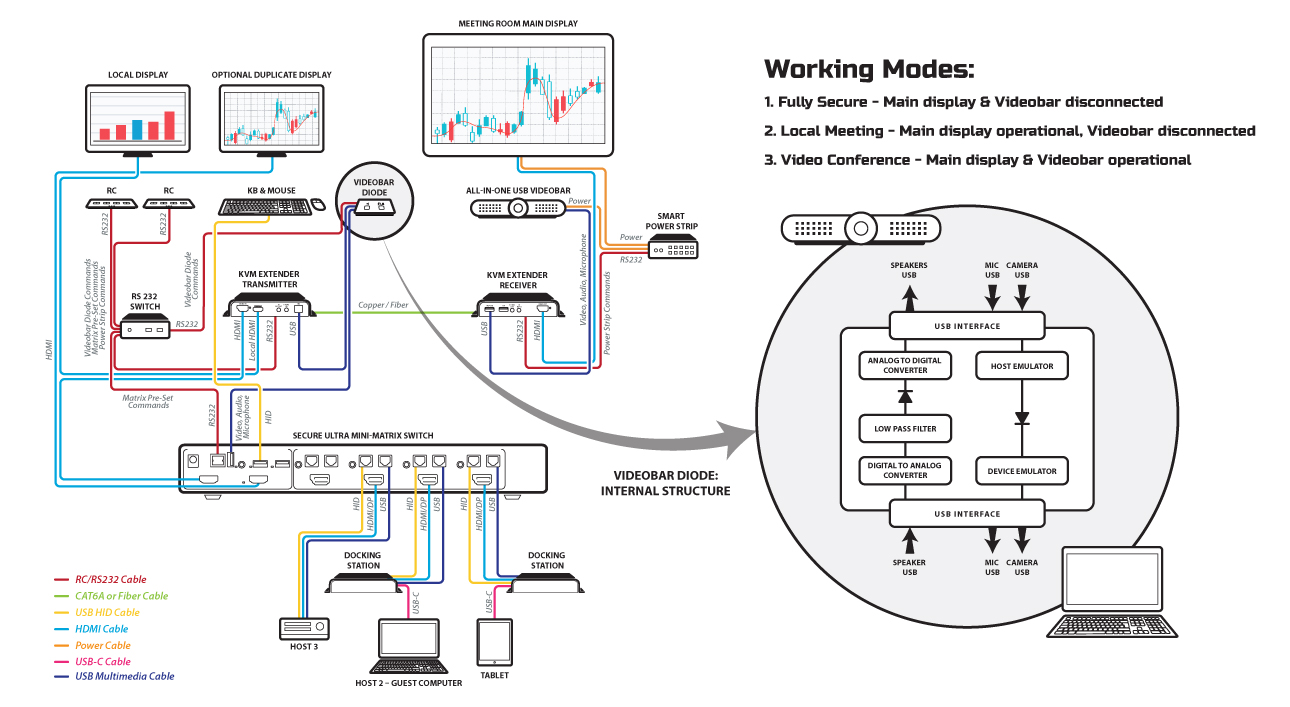
HSL’s SoundSentry solution for secure meeting rooms provides encompassing protection for even the most sensitive meetings. The solution provides the highest security for the three typical types of meetings: videoconferencing, local presentation, and local discussion. The SoundSentry solution includes these key components for securing meetings:
Videobar – A specially designed videobar that is immune to data leakage through wireless attacks and storage of information to internal memory.
SC42PHU-4/SC82PHU-4 Combiner – A NIAP compliant completely secure KVM Combiner switch with advanced multi-view capabilities. Note: SoundSentry is compatible with HSL’s secure product line of Combiner and Mini-Matrix products.
Videobar Diode – An audio and webcam diode that prevents inadvertent microphone and video transmissions, high-frequency modem data exfiltration, and enforces unidirectional flow of all data streams to prevent data leaks.
Multi-Domain Remote Control – Invoke meeting room presets for local conferences, videoconferences, and classified conversations at the push of a button.
SmartSwitch Power Strip – Provides or cuts power to the Videobar, Videobar Diode, and display screens at the push of a remote-control button to provide the proper environment, considering the security level of the meeting.
AQB (Active Quiet Box) – The ultimate eavesdropping protection for smartphones, providing physical anechoic sound isolation and noise obfuscation methods.
Key Benefits:
- Securely share peripherals across different security domains: Securely share peripherals between computers that belong to different security classification levels while keeping the highest possible data separation security.
- Prevent information leaks: Eavesdropping attempts are quashed using the AQB and the Videobar Diode. Data leaks are prevented using NIAP PP4.0 switches and devices
- Smartphones are not left unattended: Keep the smartphone in the meeting room in the AQB, under the user’s watchful eye.
- Secure any type of meeting: The SmartSwitch Power Strip along with the powerful Multi-Domain Remote control ensure that peripheral devices can be used without concern or prior vetting.